D.I.O.R. - A Model for Information Security Organization
Information security covers a lot of ground and the organization to support it needs to as well
Clearly defined responsibilities and scope of authority for security organizations vary widely across different companies and industries. To help address this challenge, I have developed an organizational framework for the information security function. As a model, this should be considered a starting point for adapting to a particular environment, not a set-in-stone guide as to the division of responsibilities, nor should it be considered all-encompassing in defining every possible function to be performed.
In organizing and staffing your security function, be sure to consider the personalities and interests of the people you are hiring. Not all security professionals are identical, and just as in the medical profession, security professionals tend to gravitate toward particular subspecialties based on their personalities and interests. Trying to make every security professional a generalist is a recipe for mediocracy and failure, likewise, an information security organization without distinct responsibilities and staff to perform them is no organization at all.
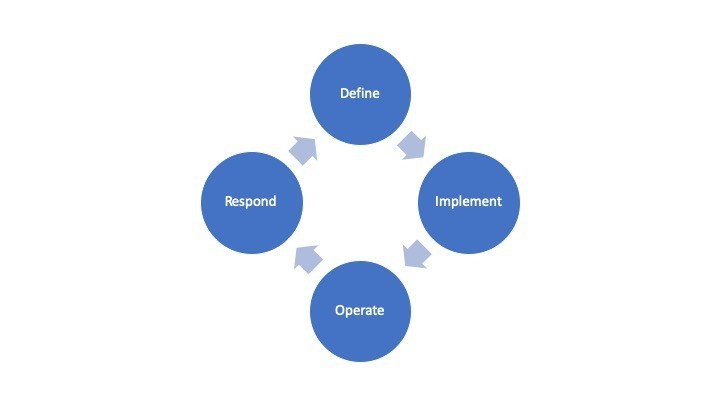
D.I.O.R.
The acronym DIOR stands for what I consider the key responsibilities of any security organization – Define (the risk & plan), Implement (the plan), Operate (the plan), and Respond (to incidents). How these components are organized, as departments within the overall security organization, or spread across multiple departments in a matrixed fashion, is highly dependent on where Information Security sits within the organization and the scope of authority of the Chief Information Security Officer (CISO).
Define
The overarching goal of any security organization should be to defend the brand and operations of the business from cyber threats by implementing a risk-based security program and plan. To define and maintain this program is the focus of the “Define” team, which is usually led by the CISO or the designated head of security. The Office of the CISO is also a term that is used to describe those who are on the Define team.
To accomplish the objective of “Define”, the following functions should be considered:
Understand the mission and objectives of the organization, as well as its operating constraints and regulatory requirements
Identify the critical assets of the organization, including systems and data
Determine the likely threats to the organization and its assets
Develop the policies and controls needed to address these threats
Monitor the effectiveness of, and adherence, to the controls in reducing risk and update risk plans accordingly
Train users on relevant cyber risks, maintain ongoing awareness, and test that awareness to ensure the training is effective
Govern the program by developing and maintaining relationships with key stakeholders, gaining consensus and support on the program and plans, and reporting progress
Implement
Implementation of security organization is accomplished through the implementation of security controls, processes, and technologies, which are integrated into the business environment. A common failing of information security is to introduce controls without consideration of the impact that they have on business/IT operations, worker productivity, or ongoing support cost.
To accomplish the objective of “Implement”, the following functions should be considered:
Evaluate/recommend control technologies and processes needed to meet policy requirements and integrate them into the business environment
Keep abreast of changes in technologies, processes, and the business that impact organizational security
Review/approve changes in the organization’s technology environment
Develop secure architectures for technology deployment, aligned to the business needs of the organization
Develop standards for the secure configuration of IT/IS products and services and update them annually and as needed
Work with IT operations in the implementation and configuration of security-related technologies
Operate
Operating security technologies effectively is a requirement all too often given short shrift in many organizations, and as a result, expected gains in risk reduction are rarely achieved. Centralizing security operations, and considering the cost of this in technology/process decisions, ensures that costs/benefits are realistically addressed in the evaluation of alternatives.
To accomplish the objective of “Operate”, the following functions should be considered (this is much larger than it looks due to the number of technologies typically deployed):
Operate and monitor the security suite of tools to prevent, detect and respond to intrusions, attacks, and vulnerabilities
Investigate events, raising confirmed or suspected intrusions to the Respond team as appropriate to the risk
Coordinate with IT operations (internal or outsourced) to track and remediate identified issues and vulnerabilities
Respond
A security program that has not prepared for the eventuality of failure is a failed security program. Incidents are inevitable in any security organization, regardless of size or budget. The degree to which organizations are prepared for these events is what determines whether the organization survives or suffers significant costs or even business failure. A common flaw in security organizations is to not staff for response/recovery as a dedicated function, which is to say that preparation is ad hoc at best as it is left to the rest of the organization.
To accomplish the objective of “Respond”, the following functions should be considered
Investigate possible attacks as raised by the Operate team and coordinate response, remediation, and recovery as appropriate
Plan and prepare for likely attack scenarios and train participants on what to expect and how to respond
Monitor operational threat intelligence and alert the Define team as needed to significant new threats
Test the resiliency of the organization and effectiveness of controls on a periodic basis through internal and external testing
Prepare and coordinate outside resources as needed to support response plans and activities